Introduction
In today’s digital age, website security is paramount. One often overlooked yet highly effective method to bolster your site’s defenses is by implementing a .well-known/security.txt file. This file serves as a beacon for security researchers, allowing them to report vulnerabilities directly to you in a standardized and secure manner. In this article, we’ll explore the importance of a security.txt file, its structure, and the significance of GPG signing it to enhance your website’s security.
Understanding the .well-known/security.txt File
What is a .well-known/security.txt File?
A .well-known/security.txt file is a text file hosted on your web server that provides contact information and guidelines for reporting security vulnerabilities. It’s an essential tool for establishing a clear communication channel between website administrators and security researchers.
Why is a .well-known/security.txt Important?
- Facilitates Vulnerability Reporting: It provides a standardized way for security researchers to report issues.
- Enhances Trust: Shows your commitment to security, building trust with users and researchers.
- Reduces Risk: Early identification of vulnerabilities can prevent potential exploits.
- Compliance: Some regulations and industry standards require having such a file in place.standards require having such a file in place.
Creating a .well-known/security.txt File
Basic Structure of a Security.txt File
A security.txt file typically includes several key sections:
- Contact Information: How researchers can reach you.
- Encryption: A PGP/GPG key to encrypt the vulnerability report.
- Acknowledgements: Recognizing researchers who report vulnerabilities.
- Policy: Guidelines for reporting vulnerabilities.
- Hiring: Information about security-related job opportunities.
- Signature: A digital signature to verify the authenticity of the file.
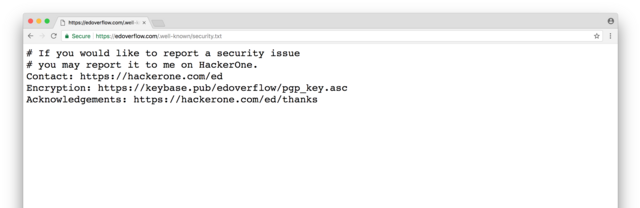
Example of a Security.txt File
Contact: mailto:[email protected]
Expires: 2024-12-05T23:00:00.000Z
Encryption: https://example.com/pgp-key.txt
Preferred-Languages: en
Canonical: https://example.com/.well-known/security.txt
How to GPG Sign Your Security.txt File
Generating a GPG Key
- Install GPG: Ensure GPG is installed on your system.
- Generate a Key Pair: Use the command
gpg --full-generate-keyand follow the prompts. - Export Your Public Key:
Use gpg --armor --export [email protected]to get the public key.
Signing the Security.txt File
- Create a Signature: Use
gpg --output security.txt.sig --detach-sign security.txtto sign the file. - Verify the Signature: Use
gpg --verify security.txt.sig security.txtto verify the signature.
Importance of GPG Signing Your Security.txt File
- Authenticity: Ensures the file hasn’t been tampered with.
- Trust: Builds trust with researchers who need to verify your identity.
- Integrity: Protects against unauthorized modifications.
Implementing Your .well-known/security.txt File
- Create the Directory: Ensure the
.well-knowndirectory exists on your server. - Upload the File: Place your
security.txtfile and the signature in the.well-knowndirectory. - Test the Accessibility: Verify that
https://yourdomain.com/.well-known/security.txtis accessible.
FAQs
What is the primary purpose of a security.txt file? The primary purpose is to provide a standard method for security researchers to report vulnerabilities to website administrators securely.
How often should I update my security.txt file? Update your security.txt file whenever there are changes to contact information, policies, or the expiration date.
Why is GPG signing important? GPG signing ensures the integrity and authenticity of the security.txt file, preventing unauthorized modifications.
Where should the security.txt file be located?
The file should be placed in the .well-known directory on your web server, accessible via https://yourdomain.com/.well-known/security.txt.
Can I include additional information in my security.txt file? Yes, you can include additional sections such as job openings, acknowledgments, and any other relevant information.
What should I do if I receive a vulnerability report? Acknowledge receipt of the report, assess the vulnerability, and take appropriate action to mitigate the risk.